Fortigate / FortiAP
This page explains the Captive Portal configuration for Fortigate hardware and authentication via IronWiFi.
IronWiFi Console Configuration
- Log into the IronWiFi console or register for free
- Create a new network
- After that, create a new captive portal, with vendor FortiGate
Access Point Configuration
You will need FortiOS v5.6 or above. This guide is based on FortiOS v7.4
Please log in to your FortiGate web interface and click User & Authentication > RADIUS Servers on the left menu. Click + Create New and configure with:
- Name - guestradius
- Primary Server - get this value from the IronWiFi console
- Primary Shared Secret - get this value from the IronWiFi console
- Secondary Server - get this value from the IronWiFi console
- Secondary Shared Secret - get this value from the IronWiFi console
- Authentication Method - Specify
- Method - PAP
Click OK to Save.
You will need to configure Radius custom port number and add accounting servers. It is only possible in the CLI.
Click on guestradius server and click Edit
In the Additional Information section on the right, click on >_ Edit in CLI and issue the following commands:
set radius port <your auth port>
set acct-interim-interval 600
config accounting-server
edit 1
set status enable
set server "<your primary server IP>"
set secret <your secret>
set port <your accnt port>
end
config accounting-server
edit 2
set status enable
set server "<your secondary server IP>"
set secret <your secret>
set port <your accnt port>
end
end
end
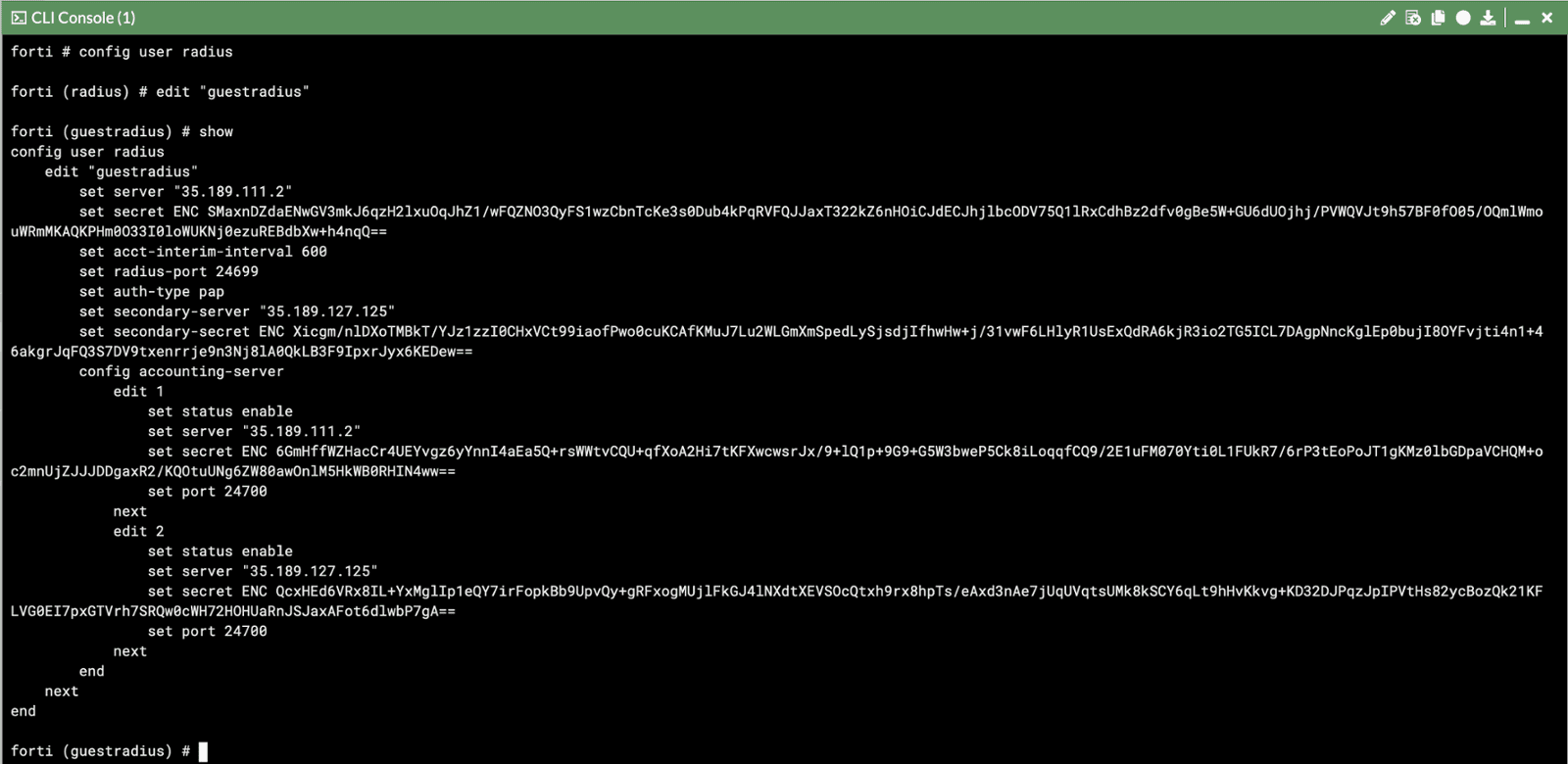
Your config should look similiar to the above.
Close the CLI window and navigate away from the edit page - do NOT press OK as it will overwrite the settings that you have just changed in the CLI.
Next, click on User Groups and Create New. Configure with:
- Name - guestgroup
- Type - Firewall
Under Remote groups click Create New and under Remote Server choose guestradius. Click OK to Save.
Next, click Policy & Objects > Addresses. Click Create New > Address. Configure with:
- Category - Address
- Name - guestonline
- Type - IP/Netmask
- Subnet / IP Range - 10.1.0.0/255.255.255.0
- Interface - any
- Show in Address List - Enabled
Click OK to Save. Next, click Create New > Address again and configure with:
- Category - Address
- Name - Your splash page's hostname
- Type - FQDN
- FQDN - Your splash page's hostname
Click OK to Save.
Next, under Addresses click Create New > Address Group. Configure with:
- Category - IPv4 Group
- Group Name - guestwhitelist
- Members - click the + button and select all the domains you added earlier.
Click OK to Save.
If you have Fortigate AP, proceed with adding the SSID as per below, if you want to configure a separate interface / VLAN that will allow you to connect other vendor's IP, please skip to Interface Configuration
Next, click WiFi & Switch Controller > SSID on the left. Click Create New > SSID. Configure with:
- Interface Name - guestwifi
- Type - WiFi SSID
- Traffic Mode - Bridge
- Address - 10.1.0.1/255.255.255.0
- DHCP Server - Enabled
- DNS Server - Same as Interface IP
- SSID - Guest WiFi (or whatever you wish)
- Security Mode - Captive Portal
- Portal Type - Authentication
- Authentication Portal - External: get this URL from the IronWiFi console
- User Groups - guestgroup
- Exempt Destinations / Services - guestwhitelist
- Broadcast SSID - Enabled
- Block Intra-SSID Traffic - Enabled
- Redirect after Captive Portal - Specific URL: get this success URL from the IronWiFi console
Click OK to Save.
Follow the paragraph section below only if you are configuring an interface / VLAN that your non-Fortigate AP will be connecting to in bridge mode !
Click on Network > Interfaces, select interface you want to use for captive portal, click Edit
Configure with:
- Addresing Mode - Manual
- IP / Netmask - 10.1.0.1/255.255.255.0
- DHCP Server - Enabled
- DNS Server - Same as Interface IP
- Security Mode - Captive Portal
- Portal Type - Authentication
- Authentication Portal - External: get this URL from the IronWiFi console
- User Groups - guestgroup
- Exempt Destinations / Services - guestwhitelist
- Redirect after Captive Portal - Specific URL: get this success URL from the IronWiFi console
Next, under IPv4 Policy click Create New. Configure with:
- Name - guestwifi
- Incoming Interface - Guest WiFi (guestwifi) OR the interface you have selected for the captive portal if you are using 3rd party AP
- Outgoing Interface - wan1 (your WAN connection)
- Source - all
- Destination Address - guestwhitelist
- Schedule - always
- Service - ALL
- Action - ACCEPT
- Enable this policy - Enabled
Click OK to Save. Click Create New again and configure with:
- Name - guestwifionline
- Incoming Interface - Guest WiFi (guestwifi) OR the interface you have selected for the captive portal if you are using 3rd party AP
- Outgoing Interface - wan1 (your WAN connection)
- Source - guestonline
- Destination Address - all
- Schedule - always
- Service - ALL
- Action - ACCEPT
- Enable this policy - Enabled
Click OK to Save.
You need to configure DNS server and get the trusted SSL certificate to avoid warnings during the captive portal authentication and redirection process.
Go to Network > DNS Servers (if you don't see that option, you need to enable it in System > Feature Visibility)
In DNS Service on Interface section click on Create New
Select interface your captive portal is on, select Mode - Recursive,click OK to save.
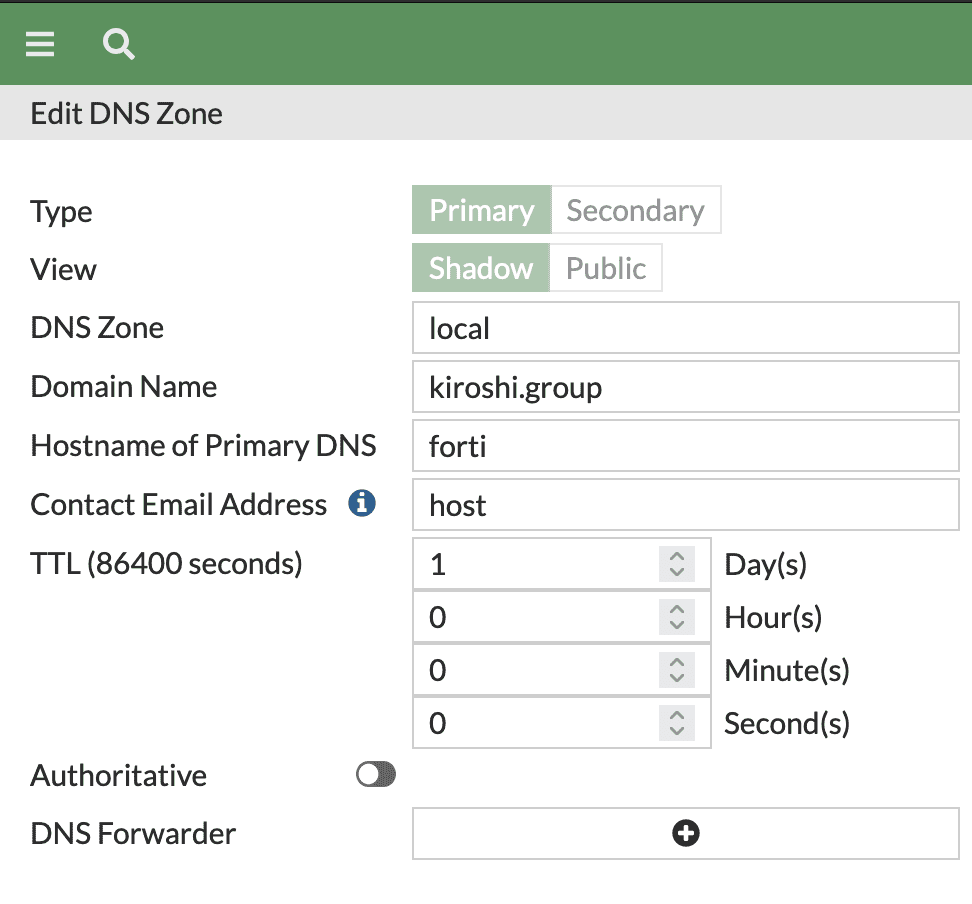
In DNS Database section click on Create New and configure with:
- Type - Primary
- View - Shadow
- DNS Zone - local
- Domain Name - <your domain name> - you must have administrative access to that domain as you will have to obtain valid SSL certificate for it
- Hostname of Primary DNS - <your hostname> - together with your domain name it will form the FQDN that you will use for the redirection
- Authoritative - disabled
Below in the DNS Entries section, click on Create New and configure with:
- Type - Address (A)
- Hostname - the same Hostname you have configured above
- IP Address - <IP Address of your Captive Portal Interface>
- Status - enabled
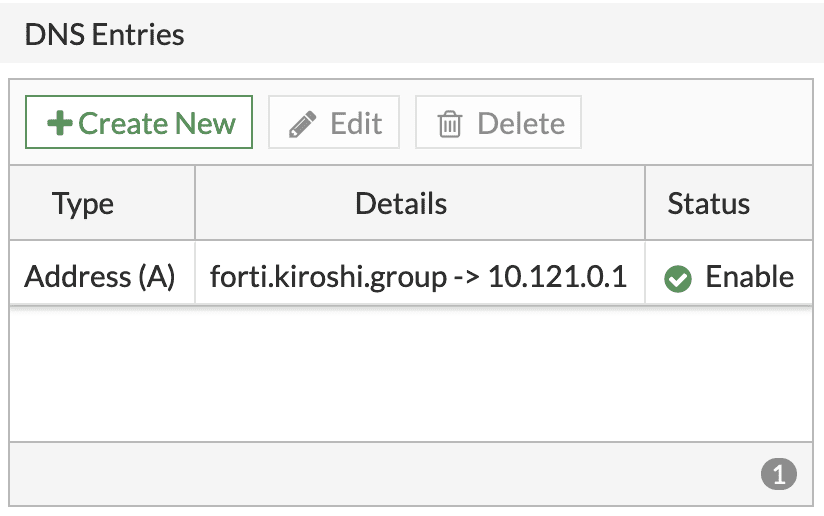
Click OK to save.
Go to System > Certificates and Import a valid SSL certificate that matches your FQDN or Create one using built-in ACME Let's Encrypt.
To finish, we need to enable secure redirections using the valid SSL certificate, enable HTTPS redirections and add FQDN we are using as the redirection URL.
Open CLI and issue the following commands:
config user setting
set auth-cert "<name of your valid SSL cert>"
set auth-secure-http enable
end
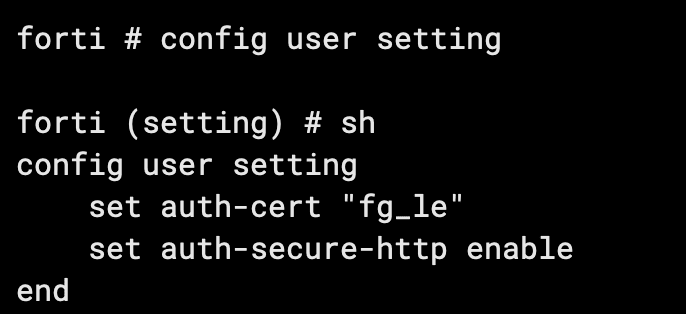
config firewall auth-portal
set portal-addr "<your FQDN>"
end
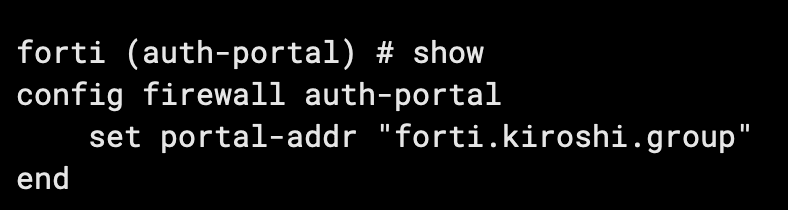
The configuration is now complete.
Related Articles
FortiGate wireless LAN controller - Passpoint Configuration
Prerequisites Access to the FortiGate CLI as a user with administrative privileges. Information about the assigned RADIUS servers (Server IP address, port numbers, shared secrets): Access to the IronWiFi Management Console - Sign in or Open Account ...Using RadSec Secure Radius on Fortigate
Enable RadSec support in IronWiFi Console and obtain your RadSec Certificate Bundle Go to this link to enable RadSec on your account and download your secure certificate bundle. Configure Fortigate / FortiAP to use IronWiFi Secure RadSec Servers This ...pfSense with Captive Portal
This page explains different configuration scenarios for pfSense Firewall and authentication with IronWiFi. IronWiFi Console configuration Log in to the IronWiFi Console From the menu, go to Network -> Captive Portals -> New Captive Portal Fill in ...SonicWall Captive Portal
This page explains the configuration of SonicWall devices to work with IronWiFi Captive Portal and Captive Portal Authentication. Log in to your SonicWall firewall and click Manage at the top. On the left menu, click on VPN > Base Setting and ensure ...Aruba Virtual Controller & Captive Portal
This page explains basic configuration for Aruba Virtual Controller and external Captive Portal with RADIUS authentication. Sign-in to the Aruba Administration console Navigate to Network -> Edit and open configuration settings of a network that ...