SCEP with Intune
The Simple Certificate Enrollment Protocol (SCEP) is a protocol that allows devices to easily enroll for a certificate by using a URL and a shared secret to communicate with a PKI.
This is an example of setting up SCEP with IronWiFi and Microsoft Intune.
What do you need ?
- owner_id - owner id is a unique identifier of your IronWiFi account that can be found in the URL when you're logged in, it should look similar to this - abcdefg12345678 or domain-abcd1234
- region - region where your data resides and authentication requests are processed - us-east1, console, asia-northeast1, etc
-
SCEP Server URL - build the URL in this format - https://{% raw %}{{region}}{% endraw %}.ironwifi.com/api/{% raw %}{{owner_id}}{% endraw %}/certificates/scep.
Note that for Windows profiles, "/scep" needs to be removed since it is appended by the Intune application automatically - https://{% raw %}{{region}}{% endraw %}.ironwifi.com/api/{% raw %}{{owner_id}}{% endraw %}/certificates
-
IronWiFi CA Certificate - certificate of the CA signing the CSR requests. This can be downloaded from this link
- Trusted IronWiFi Server Certificate - server certificate signed by a trusted CA. This file can be downloaded from this link
- Comodo CA Certificate - certificate of the CA that signed our RADIUS server certificates. This can be downloaded from this link
!Note! Your users must exist in the IronWiFi console or the SCEP connector's User Auto-Creation option must be enabled for this to work
-
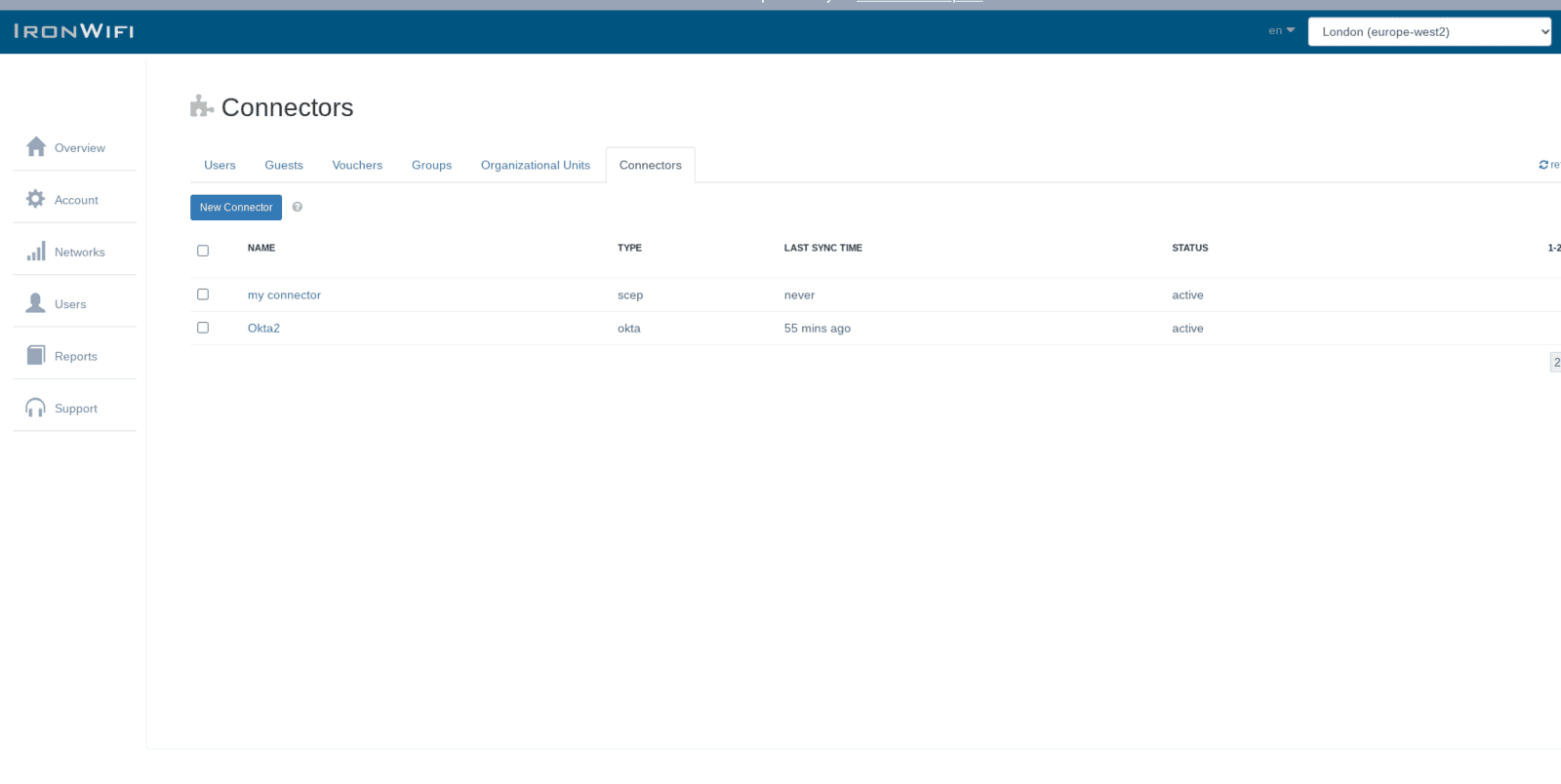
Sign in to the IronWiFi Management Console and create a SCEP connector - click on Users -> Connectors -> New Connector
2. Sign in to the Microsoft Intune management console
3. Navigate to Devices > Configuration Profiles
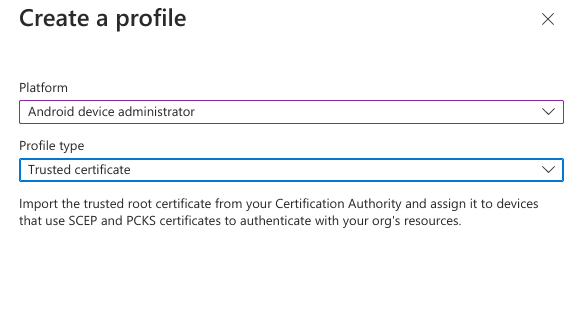
4. Click Create Policy and choose the option create a new Trusted Certificate profile with the following configuration options:
- Certificate file - ironwifi.crt (This can be downloaded from this link)
- Destination store - Computer certificate store - Root
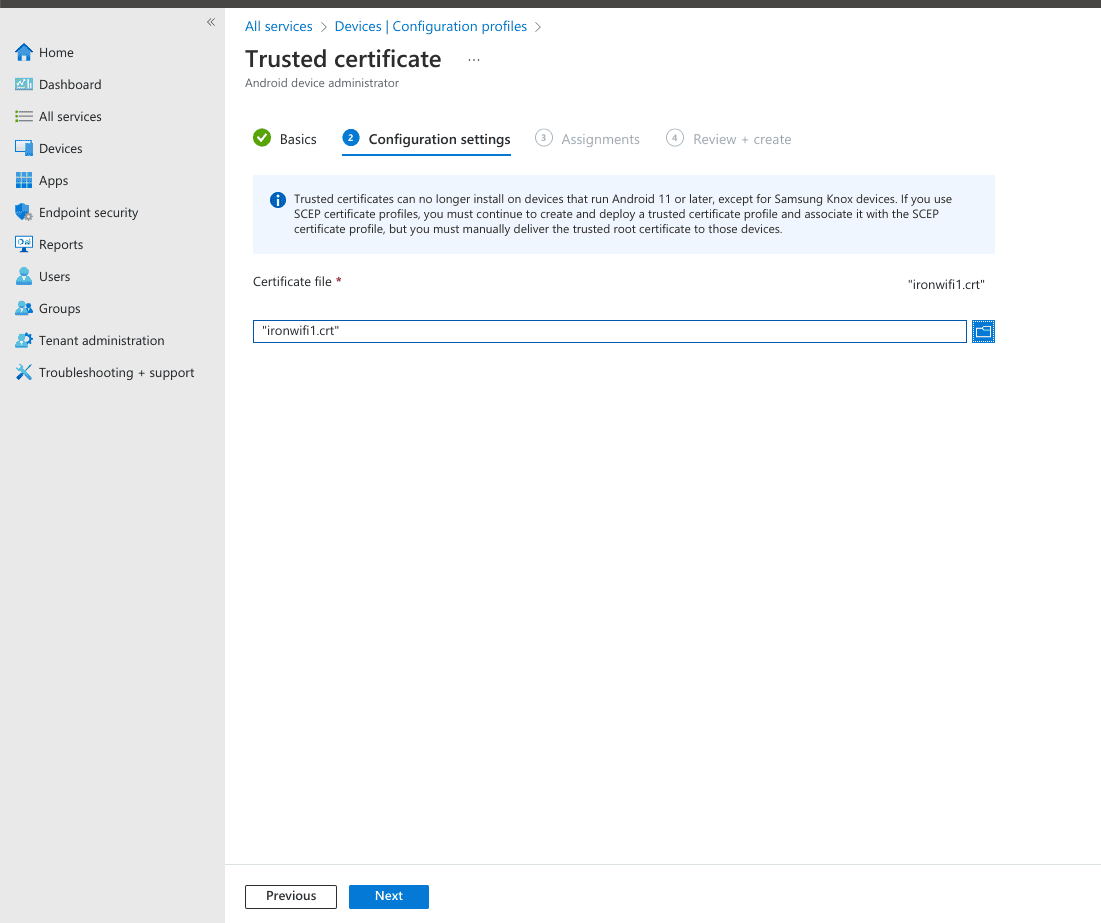
5. Create another Policy, select profile type Trusted Certificate and use the following configuration options:
- Certificate file - ironwifi_trusted.crt (This file can be downloaded from this link)
- Destination store - Computer certificate store - Root
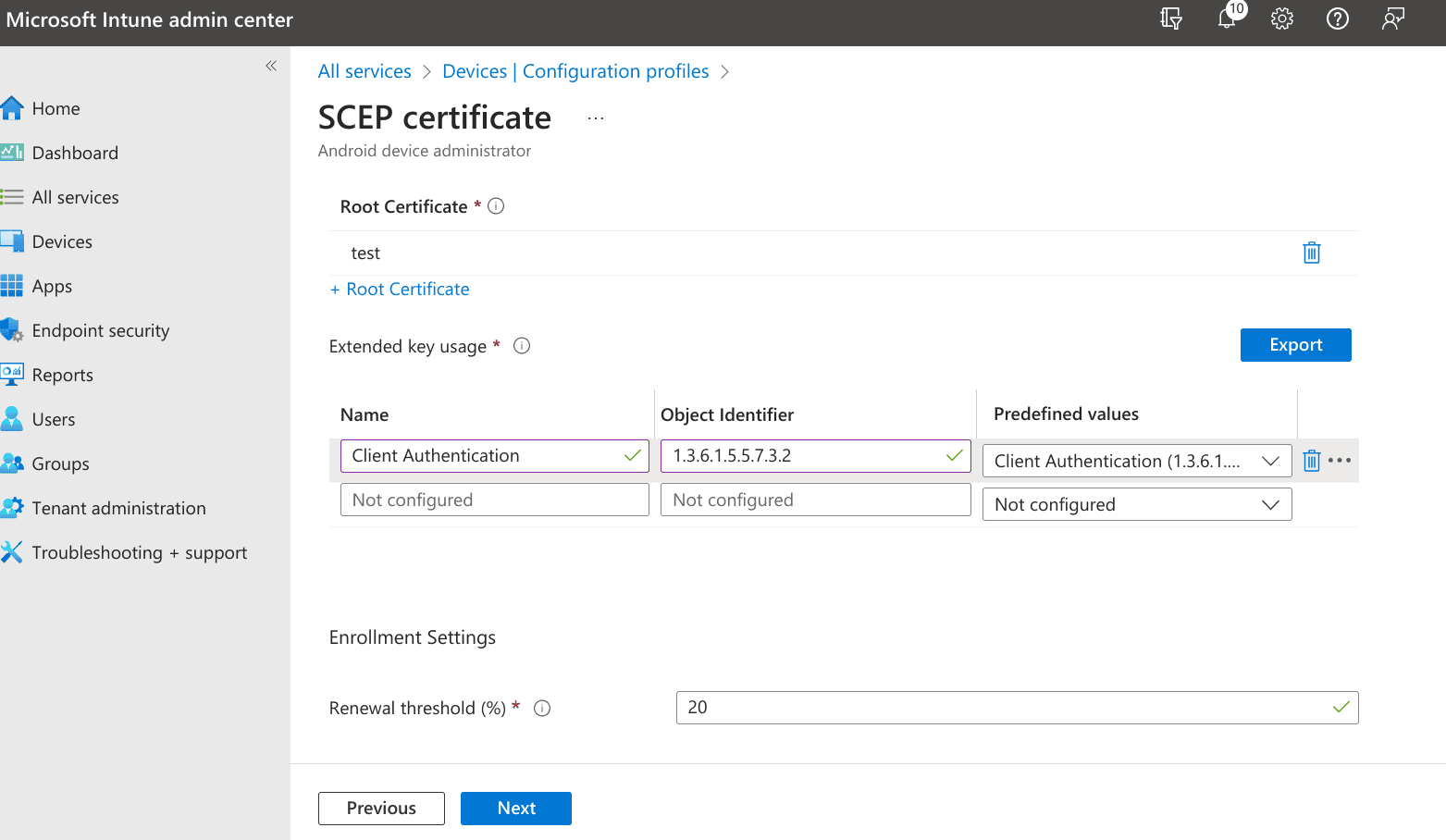
6. Create a new SCEP certificate profile with the following configuration options:
- Profile Type - SCEP Certificate
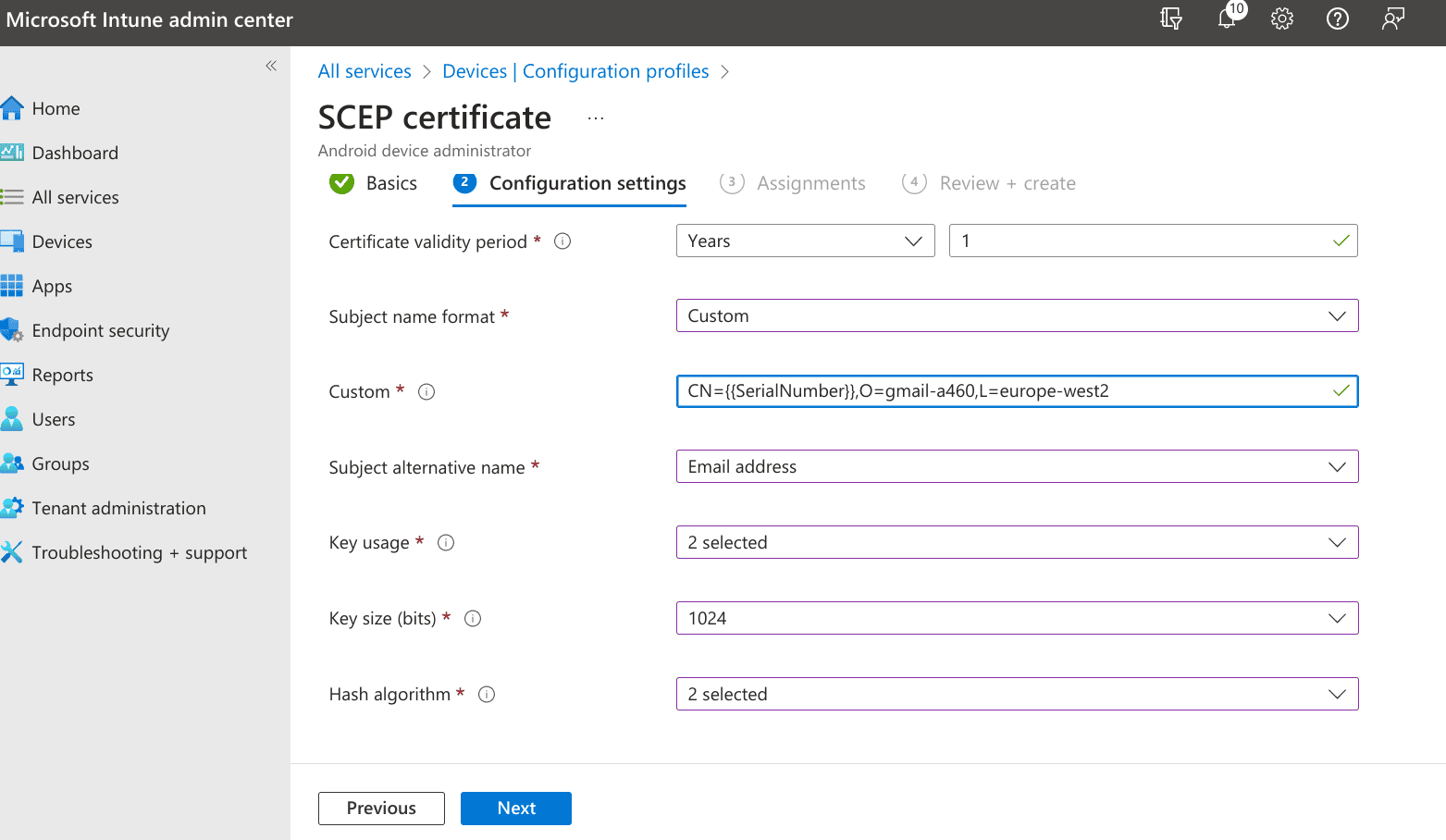
- Certificate type - User
- Subject name format - CN={% raw %}{{SerialNumber}}{% endraw %},O={% raw %}{{owner_id}}{% endraw %},L={% raw %}{{region}}{% endraw %}
- Subject alternative name - Email address = {% raw %}{{UserPrincipalName}}{% endraw %}
- Certificate validity period - 180 Days
- Key storage provider (KSP) - Enroll to Software KSP
- Key usage - Key encipherment, Digital signature
- Key size (bits) - 1024
- Hash algorithm - SHA-1, SHA-2
- Root Certificate - Your trusted certificate profile created in the fourth step
- Extended key usage -
| Name | Object Identifier | Predefined values |
|---|---|---|
| Client authentication | 1.3.6.1.5.5.7.3.2 | Client Authentication |
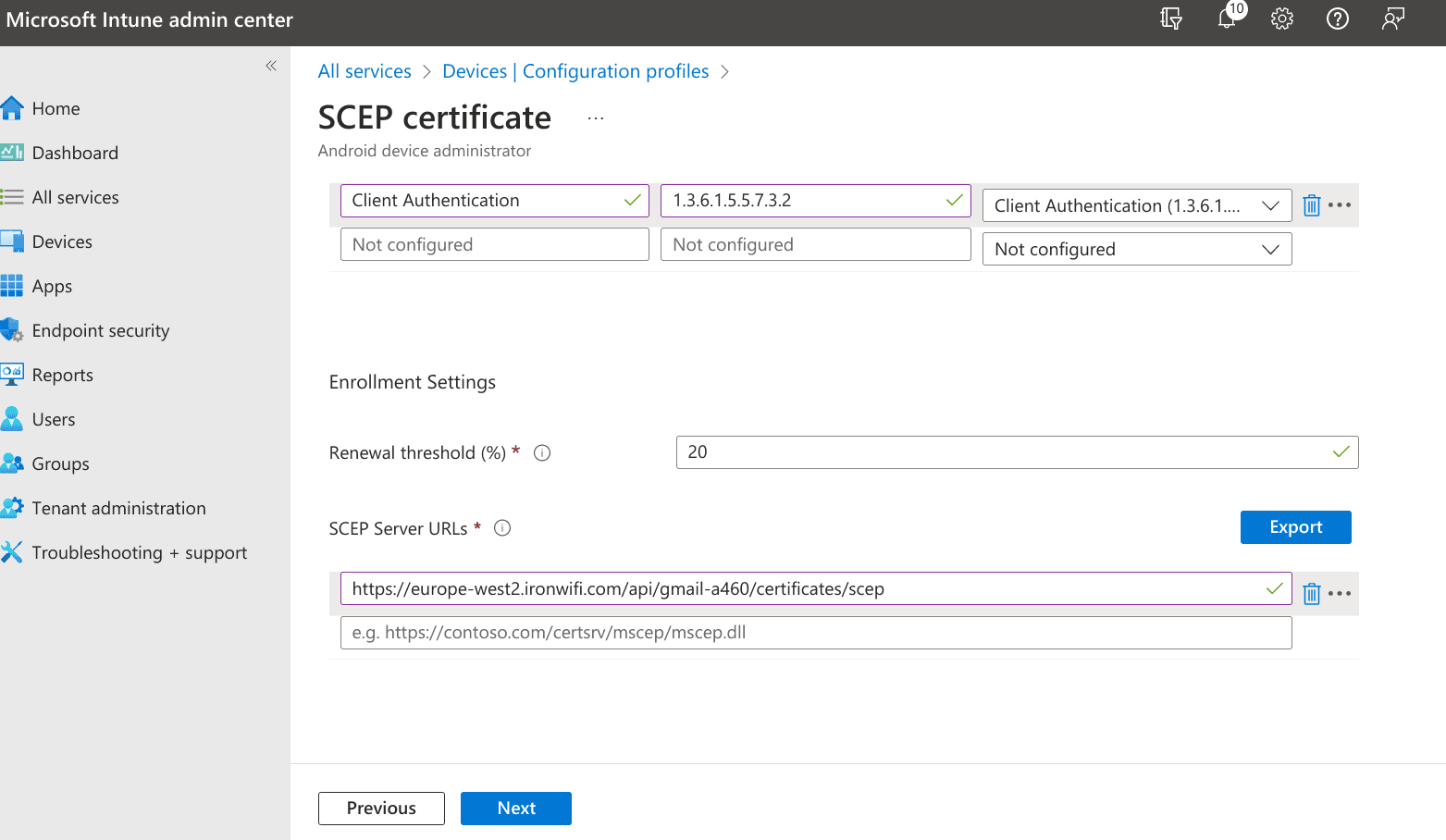
- Renewal threshold (%) - 50
- SCEP Server URL - https://{% raw %}{{region}}{% endraw %}.ironwifi.com/api/{% raw %}{{owner_id}}{% endraw %}/certificates/scep
7. Create a new Wi-Fi profile with the following configuration options:
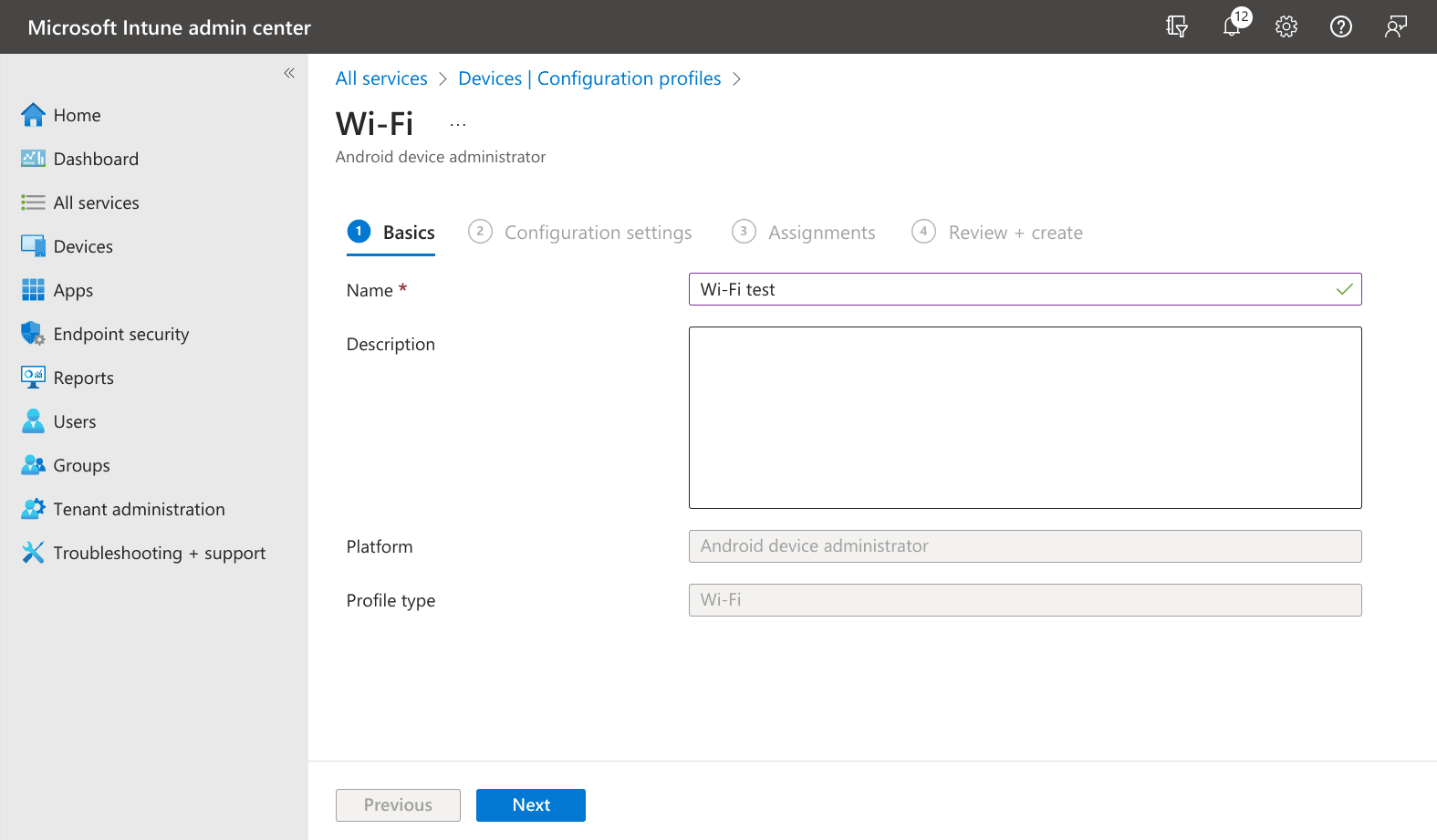
- Profile Type - Wi-Fi
- Connect to more preferred network if available - No
- Wi-Fi type - Enterprise
- Wi-Fi name - Your SSID
- Connection name - Your connection name
- Connect automatically when in range - Yes
- Connect to this network, even when it is not broadcasting its SSID - Yes
- Metered Connection Limit - Unrestricted
- Force Wi-Fi profile to be compliant with the Federal Information Processing Standard (FIPS) - No
- Company proxy settings - none
- Single sign-on (SSO) - Disable
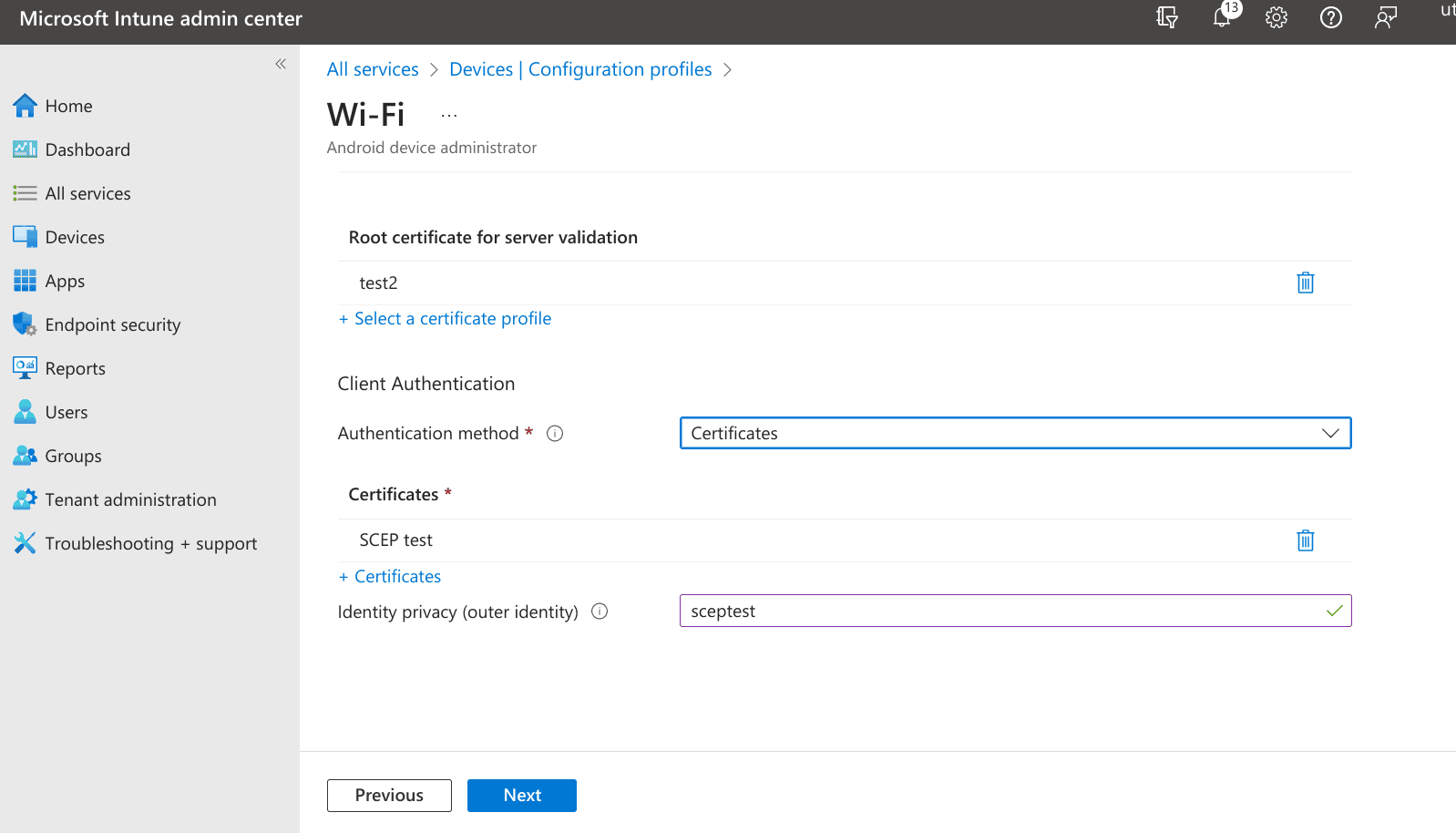
- EAP type - EAP - TLS
- Certificate server names - radius.ironwifi.com
- Root certificates for server validation - The trusted certificate created in the fifth step
- Authentication method - SCEP certificate
- Client certificate for client authentication (identity certificate) - Your SCEP certificate profile created in the sixth step
.png)
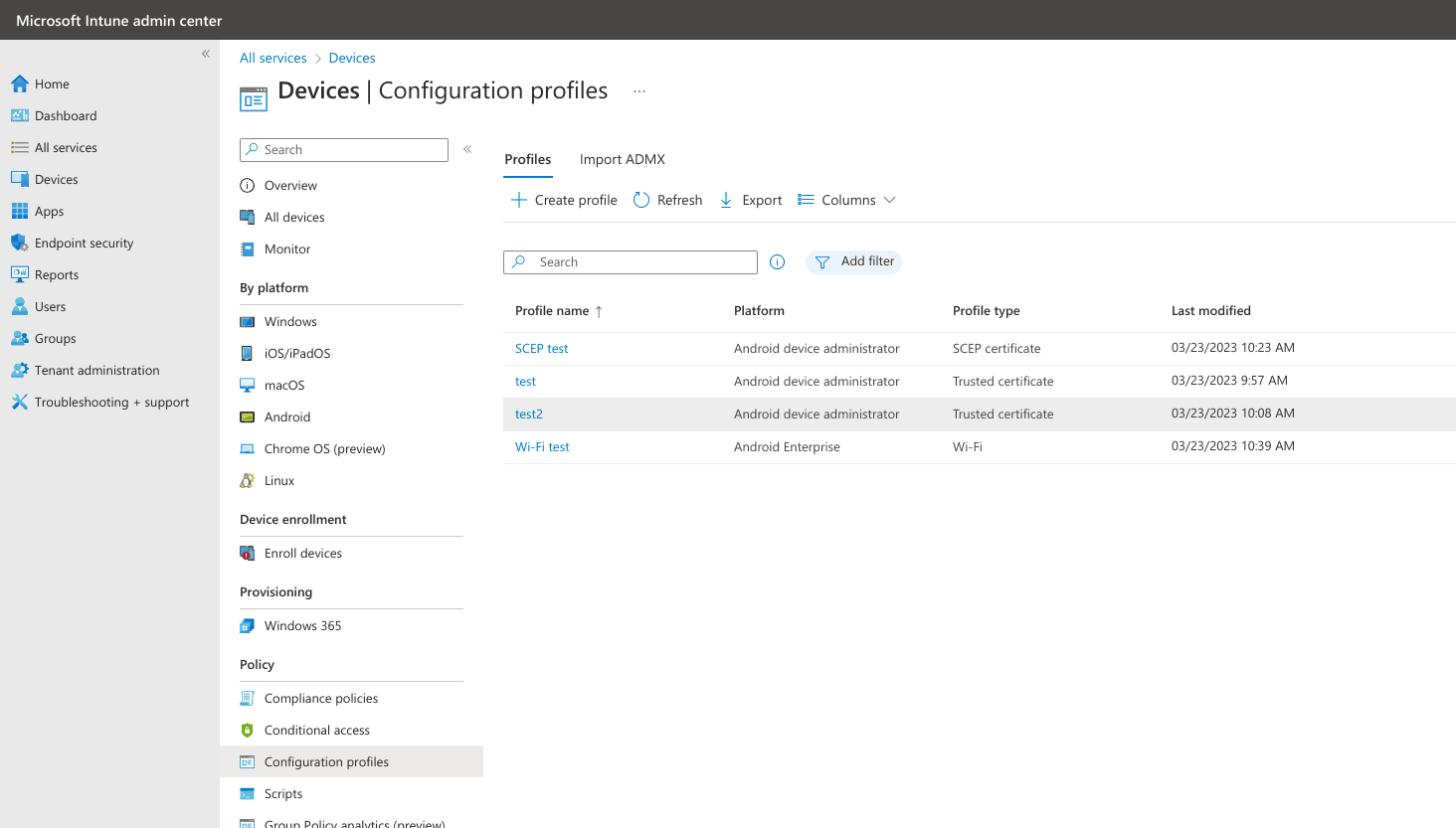
You should now see 4 configuration profiles under Devices in your Microsoft Endpoint Manager admin center
Related Articles
SCEP with Intune - IronWiFi PKI - User Auth
The Simple Certificate Enrollment Protocol (SCEP) is a protocol that allows devices to easily enroll for a certificate by using a URL and a shared secret to communicate with a PKI. This is a guide for setting up SCEP with IronWiFi's new multi-tiered ...SCEP with Intune - IronWiFi PKI - Device Auth
The Simple Certificate Enrollment Protocol (SCEP) is a protocol that allows devices to easily enroll for a certificate by using a URL and a shared secret to communicate with a PKI. This is a guide for setting up SCEP with IronWiFi's new multi-tiered ...Intune - TTLS-PAP with IronWiFi PKI
This is a guide for setting up TTLS-PAP with IronWiFi's multi-tiered HSM based Certificate Authority and Microsoft Intune to provision Windows OS based devices, using user profile. What do you need ? IronWiFi Root CA Certificate - certificate of the ...Azure
Our azure integrations allow you to import users from your Azure Active Directory, use Azure SAML authentication, set up 2FA and more. We provide instructions to help you get up and running as fast as possible, see the links below and follow the ...Implementing Private PKI with IronWiFi
Thanks to our modular PKI infrastructure we are able to offer the Private PKI for our most demanding customers. Whilst security level of our standard offering leaves nothing to be desired, we are able to offer two additional solutions for our ...